End BYOD Risks with Military-Grade Virtual Mobility

More than 80% of companies allow at least some employees to use personal mobile devices for work—and the recent movement to remote workforces has only broadened their use. The majority cite cost as the biggest driver for approving Bring Your Own Device (BYOD) policies, with an average savings of $640 per device.
But nearly 40% of organizations report experiencing a security compromise involving mobile or IoT devices, and more than 65% indicate that the incident had a major impact. And the pandemic is making matters worse. Cyberattacks are skyrocketing as cybercriminals prey on fears of the virus, creating COVID-related phishing scams to get access to sensitive personal information.
“Every single mobile device means a potential for an attack,” says Philip Goodrich, Partners & Alliances Director for Hypori Virtual Mobility, a provider of a highly secure Virtual Mobility Solution (VMS). “Employees often don’t have adequate cybersecurity enabled on their personal networks, and many are running out-of-date or unpatched operating systems on their smartphones. If an employee opens an email that they shouldn’t, uses public Wi-Fi, or unknowingly downloads an app on their phone that has malware, a hacker can gain direct access to enterprise data.”
Unfortunately, the convenience of BYOD could lead to lasting security and financial consequences. Until now, organizations have relied on Mobile Device Management (MDM) software solutions put in place by IT departments to monitor, manage, and secure employees’ devices. If an employee loses their device or is hacked, IT will perform a remote wipe, removing all data on the device. But these tools don’t go far enough because data could be accessed before an employee realizes what happened and alerts their employer to take action.
A better solution is a tool like Hypori Virtual Mobility (Figure 1) that takes a “zero trust” approach.
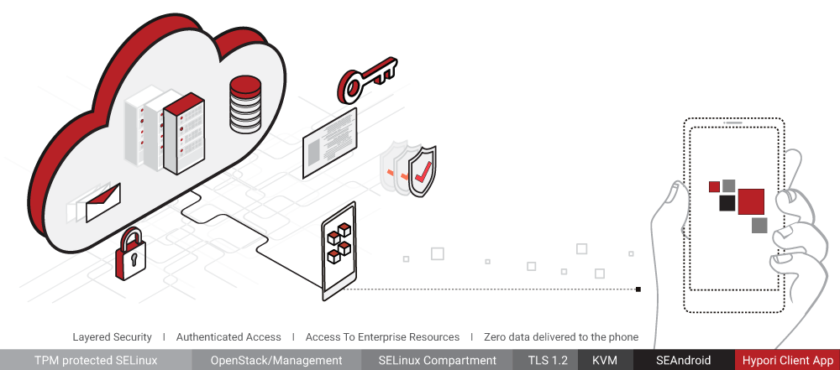
“We use proprietary technology that sends an encrypted pixel stream to the device. This allows end-users to see and interact with data in a secure manner,” says Goodrich. “But the data never resides on the device. As a result, there’s never any unauthorized access to enterprise data or systems.”
Deploying a Secure Virtual Mobile Infrastructure
End-users install the Hypori app on their existing Android, iOS, or Windows 10 device, providing them with secure access to enterprise data. The Hypori Administrative Console enables system administrators to easily manage provisioning, authentication, virtual device hosting, and APIs. And the virtual solution keeps corporate data separated from personal data on the end-user’s device.
“Why would you use an unsafe, inconvenient, costly, and administratively cumbersome #MDM solution when you could use virtual #mobile infrastructure?” @Hypor_VM via @insightdottech
The solution uses multilayer security to stop network breaches. “Multilayer security uses several components at different layers and attack vectors,” says Goodrich. “Each layer has security measures in place, and each individual defense component has a backup in case one of the initial components or layers is compromised. The layers work together to stop intruders from breaching your networks. This is important because the cyber-threat landscape continues to evolve and expand.”
In addition to heightened security, Hypori saves organizations money by eliminating complex management systems with a single console. It also increases productivity for IT staff and end-users by offering a familiar smartphone environment for an intuitive user experience. And it’s fast!
“The advantage is everything runs at data center connectivity speeds,” says Goodrich. “The application response and performance doesn’t rely on the end-user device processor. Plus, our application is so lightweight that there’s minimal impact on the device processor and battery life.”
Organizations can choose a cloud-delivered SaaS model that is billed per user, making it easy to scale. Or they can select to have the appliance installed in their data center, which is common in industries that have high levels of regulations, such as healthcare, financial services, and government.
The Hypori appliance is built with Intel®-powered servers and storage. “Our application sophistication requires state-of-the-art processing, power, memory, and storage capabilities,” says Goodrich. “We looked at several system options, but only Intel was able to meet all of our requirements. Working with Intel helps meet Hypori’s stringent requirements to deliver the highest-quality product.”
Hypori Takes Virtual Mobility to a New Level
Hypori recently helped a home healthcare provider improve its patient care procedures. To streamline home visits, the organization distributed tablets to patients that were preloaded with the Hypori app. “Healthcare is the number-one most cyberattacked industry because their data centers store highly sensitive and valuable Protected Health Information (PHI). And these breaches are costly, averaging $7.13 million per attack,” says Goodrich.
“When our home healthcare provider client comes to the patient’s house for a home visit, they access the device, open the Hypori app, and log in to see the patient’s records, treatment plans, medication schedules, and medical directives,” says Goodrich. “Healthcare workers are empowered to do their jobs and no longer have to carry around a lot of devices. When they complete their visit, they log out of the Hypori app and return the device to the patient who goes back to using it for regular activities.”
Hypori also helped the U.S. Department of Defense secure its communications capabilities, enabling access to government classified and unclassified resources for hundreds of thousands of service members and the government civilian workforce. Previous solutions were difficult to maintain, too bulky for portable use, and too costly to deploy at scale.
Goodrich expects solutions like Hypori Virtual Mobility to become the go-to approach for organizations. “Why would you use an unsafe, inconvenient, costly, and administratively cumbersome MDM solution when you could use virtual mobile infrastructure?” he asks. “VMI is not brand-new, but the Hypori solution is transformative. Our solution, which employs military-grade security, is eagerly adopted by end-users, is centrally managed, and satisfies all of the regulatory compliance requirements.”