Simplify Secure, UEFI-Based IoT Firmware Updates
In the age of the Internet of Things (IoT), where everything is becoming connected, each connection point can be viewed as a “Hack This” sign for the bad guys. To prevent this, developers need to be sure that all firmware and associated patches are kept up to date with verified and secure revision control. Any unpatched or outdated firmware can allow access to critical system functions.
Unfortunately, this need to keep firmware updated often goes overlooked by the development team after a product has shipped. In many cases this is due to the resources required and complexities involved. But what if the whole process of updating and securing firmware remotely or over the air (OTA) could be standardized and encapsulated within an easy-to-use, reliable solution that works seamlessly with your underlying hardware? It turns out that such a solution is already in hand.
Software/Firmware Teams Are Often on the Hook for Security
Whether it's a bug, vulnerability, or some other issue in an embedded system, responsibility for the fix often seems to fall on the software/firmware team. The logical reason is that it's a lot easier to make a fix in software than it is in hardware – and far less expensive.
From a security perspective, eliminating vulnerabilities is often the responsibility of software, as just about every remote hack is made through a weakness in software or firmware. Why? Because issuing an attack through firmware (remotely or otherwise) is far simpler than through hardware, which requires physical presence.
These firmware security exploits can potentially affect millions of devices if they're connected to the IoT. An effective exploit of a device's firmware may also provide access to private information, corporate data, and even medical information. Furthermore, if the hackers gain access to the operating system (OS), they can completely take over the device and compromise the entire network. Assuming that new exploits will continue to be discovered, the challenge is responding quickly to avoid or minimize any impact: The longer the vulnerability lingers, the more likely it is to be exploited and the more damage that can result.
By standardizing the update process, a compliant OS can apply a firmware update to any platform as easily as applying an OS driver or application update. And because the IoT device is connected, it can check for and download updates seamlessly over the air and close vulnerabilities quickly, potentially as soon as the same day the fix is released. This assumes that the developer has resolved some of the issues associated with implementing OTA updates.
Updating Out-of-Date Firmware: Development Dilemmas
With OTA updates OEMs can now remotely close firmware loopholes. But there are two challenges with respect to efficiently implementing OTA updates effectively and securely. The first is differentiating between out-of-date firmware components and those that are current within a given system. Firmware updates often require a device reset that can be costly for certain systems, so the goal is to minimize their frequency.
To identify those components that need to be updated, it's important to remember that firmware is not monolithic. Many of the individual ICs and other components on IoT devices contain their own firmware, so developers and security professionals must go beyond the BIOS to identify which of the various components can be updated.
The second challenge is determining whether new firmware releases have been verified as secure.
UEFI Update Capsule: Isolated, Secure Firmware Updates
To help designers quickly overcome these challenges and make OTA firmware updates a more natural part of the product design and support cycle, OEMs are now making use of the Unified Extensible Firmware Interface (UEFI) specification's Update Capsule technology. This isolates specific firmware components for update. When implemented in commercially available UEFI BIOS firmware solutions that are capable of monitoring updatable firmware component versions and accepting only known-good firmware releases for update, UEFI Update Capsule technology can ensure that overall system firmware remains as bulletproof as possible.
Implementing the UEFI specification allows for the extension of platform firmware by loading the UEFI driver and application images (Figure 1). When these images are loaded, they gain access to all UEFI-defined runtime and boot services.
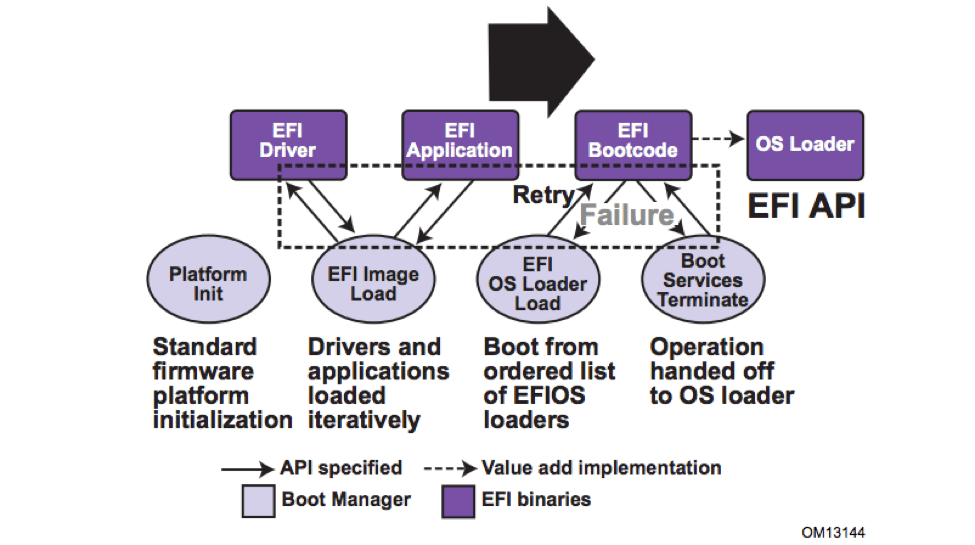
UEFI firmware delivers a table known as the EFI System Resource Table (ESRT) that describes all of the updatable firmware components on the IoT device and the versions of each. This lets the OS detect when a firmware update is available.
Of course, it's not enough to have an update if that update introduces more problems than it solves. For example, you wouldn't want to upload a “new” version that's actually older than the residing version. And you certainly don't want to upload a version that contains malware or is not intended for the IoT device's vendor.
For this reason, the UEFI capsule (including its version) is cryptographically signed with a verification key that's embedded in a flash memory device. This allows the UEFI capsule to be accessed during the boot process, before third-party code is executed by the UEFI firmware.
Through this technology, IoT device makers gain peace of mind, knowing that their products are secure. OEMs can also minimize the amount of time spent sending out patches that could otherwise be used to develop revenue-generating services.
But for developers to take full advantage of the technology, it helps if there is a readymade OTA version control and verification solution.
Closing Loopholes in Connected Embedded Devices
A company that has already developed such a solution is Insyde Software. Its InsydeH2O has been tested in hundreds of different platform types and helps IoT device developers respond quickly to firmware security exploits by enabling a simple update delivery mechanism.
The software tool takes advantage of UEFI Update Capsule technology to report the current version of each updatable firmware component in the system. The software then accepts updates that are verified and applies them to the secure environment. As noted, the ESRT reports the current versions of all updatable firmware components. Even if the OS or the local IT administrator doesn't provide connected access to firmware updates, the InsydeH20 Firmware Flash Tool utility, H2OFFT, lets the user quickly and easily update flash devices with new BIOS firmware.
InsydeH20 can be implemented in conjunction with OTA updates to ensure that IoT device firmware remains secure and up to date. It does so by locking down flash memory and letting the OS know which version of firmware is currently in operation. Verified updated versions of the firmware are then accepted by the OS. InsydeH2O then rechecks to be sure that the new version is authorized by the vendor.
No secure update process can be stronger than the protection that the processor provides for the flash device in which the firmware resides. Insyde Software has taken advantage of the features of the Intel Atom® C3000 processor to ensure secure next-generation IoT edge devices.
The Intel Atom® C3000 processor allows InsydeH2O to lock down the flash device and protect it from unauthorized modification later. Further, Insyde's BootGuard on Denverton's Innovation Engine can verify those first firmware bits before they're even executed, supporting the secure code authentication provided by the NIST-800-155 guidelines.
Make Headlines, for the Right Reasons
Combining standards-based firmware update technology with hardware security features allows OEMs to remediate vulnerabilities that exist in devices already deployed in the field. What's more, technology such as InsydeH20 proactively monitors firmware versions to ensure they are secure and up to date, freeing developers from the process of manually checking the status of each firmware component on connected devices throughout their lifecycle. Developers can now focus on the creation of value-added services, but, more important, they can dramatically reduce the likelihood of their hacked IoT systems ending up in the news.