Intrinsically Safe: Tablets for Critical Industry 4.0
Digital transformation has made its way to critical industries (CIs), where tablet PCs can now allow technicians to capture and share operational data efficiently from the field. While this is an important step toward bringing Internet of Things (IoT) capabilities to brownfield installations, it requires design and use of extremely rugged, intrinsically safe, and highly secure tablets.
By conforming to well-established international standards, designers of tablets can get to the required levels of safety using advanced packaging, system design, and thermal management techniques. Also, by using the right third-party cybersecurity software to best complement the hardware's own security capabilities, designers and users can be assured of a highly secure tablet design.
Implementing the required combination of intrinsic safety and high security in tandem ensures that a tablet intended for CI can protect sensitive equipment, information, and human operators.
Regulating Explosive Environments for Critical Industries
Applications like oil and gas, mining, the chemical industry, and industrial automation are often defined by hazardous conditions. The danger presented by potentially explosive environments results in strict safety measures and standard operating procedures for workers, likewise for electronic systems in similar environments.
To help reach and ensure an agreed-on level of safety, there are well-documented standards. The ATEX directive and International Electrotechnical Commission Explosive (IECEx) standards in the European Union, along with UL 913 in North America, define different types of explosive atmospheres and the likelihood of hazardous conditions in them, using a combination of zones, classes, and divisions (Table 1).
Electronic devices that inhabit these areas must meet certain design criteria to achieve certification from the corresponding agencies. Many of these criteria are outlined in the IEC 60079 family of standards, including flameproof enclosures, pressurization, encapsulation, powder filling, provisions against oil immersion, and overall intrinsically safe design (Figure 1). In explosive locations, all of these are intended to help minimize the concentration of heat in a system to prevent ignitions.
The rigors of certification have prevented many modern technologies from being used in these settings, including wireless connectivity, advanced processors, and batteries. As a result, CIs have largely been unable to take advantage of IoT opportunities, such as increases in efficiency, reduced downtime, and lower operating costs.
But today intrinsically safe industrial tablets are being developed that safely and securely connect CI machinery, data, and personnel. These tablets allow CI operators to integrate valuable existing equipment with business systems, without the need for retrofits or replacements.
Intrinsically Safe Tablets for Industry’s Digital Transformation
To mobilize both the CI workforce and system data, even in explosive environments, Aegex Technologies, LLC has released the Aegex10 Intrinsically Safe Tablet (Figure 2). The Aegex10 meets the requirements of ATEX/IECEx Zone 1 and UL 913 Class 1, 2, 3/Division 1 standards, which certifies it for use in locations where gas, dust, or debris are routinely present.
The Aegex10 features a 10.1” capacitive touchscreen with 1920 x 1200 Widescreen Ultra Extended Graphics Array (WUXGA) resolution. The touchscreen can be used with gloves or a stylus. The tablet is suitable for use across a temperature range of -10ºC to +50ºC and is IP65-rated against dust or fluid.
While these specifications are similar to many other tablets available on the market, Aegex engineers implemented a number of thermal management design features at the board level to help the devices achieve ATEX, IECEx, and North American certification. The first of these was selecting a quad-core Intel Atom® processor that runs at up to 2.39 GHz, but which can be throttled back to 1.8 GHz. This frequency scaling, along with the SoC's 22-nm process technology, reduces the concentration of heat that could potentially trigger an explosion.
Additional system components are also configured in a manner that minimizes thermal buildup and enables precision control over the temperature and energy level of circuits. The tablets include dual-fault tolerance so that any combination of two concurrent system failures cannot result in ignition, and also passed a drop test.
The intrinsically safe design of Aegex10 tablets enables an advanced connectivity, software, and security suite that further sets the devices apart for CI operators. From a wireless perspective, the Aegex10 supports 4G LTE, dual-band 802.11a/b/g/n/ac Wi-Fi, Bluetooth low energy (BLE), and near-field communications (NFC), as well as GPS/GLONASS for location. Ethernet, USB 2.0 (full-size), USB 3.0, HDMI, and microSDXC ports are also provided so that field technicians can interface with compatible equipment in the field.
Aegex10 tablets run the Windows 10 operating system (OS) out of the box, allowing the devices to synch seamlessly with many organizations' internal IT systems. They are also equipped with FHOOSH High-Speed Cybersecurity software, which secures sensitive data from the point of capture through its delivery to other endpoints or the cloud.
The FHOOSH software is able to ensure end-to-end data security by breaking up data into fragments, disassociating it, and then applying FIPS 140-2-compliant AES-256 encryption (Figure 3).
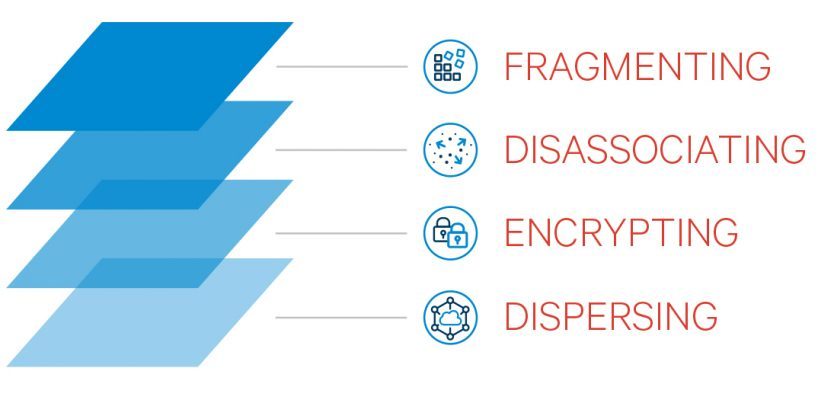
This architecture means that any data captured by an Aegex10 tablet remains in an always-protected state, removing potential vulnerabilities and providing two additional key benefits for CI operators:
- Compliance—Transmitting data over a network does not create additional compliance or auditing requirements because it is never unencrypted. The cost and time of maintaining compliance with standards like the National Institute of Standards and Technology (NIST) Cybersecurity Framework, IEC-62443, ISO 27001, North American Electric Reliability Corporation (NERC) Critical Infrastructure Protection (CIP), and others is therefore reduced.
- Speed—Transmitting data over a network is much faster because packets are fragmented and already encrypted. According to FHOOSH, transferring large and sensitive data stores can be done 8x faster than average. The software also enables applications like secure, low-latency live video streaming.
At a silicon level, Intel Atom processors also incorporate a suite of security features based on McAfee products. For instance, secure boot through McAfee Deep Defender verifies the integrity of Aegex10 tablets from bootup, and whitelisting through McAfee Embedded Control prevents any unauthorized software from running on the device.
Stepping Into Critical Industry 4.0
To date, equipment in hazardous environments has been the epitome of the “IoT edge.” Not only are these systems difficult for human operators to access, safety requirements have often isolated them from technology as well.
With advances in safety and security from companies like Aegex and FHOOSH Software, it is now possible to extract important information from these systems and share it across an organization. On-site technicians can share pictures or video in real time, or access data sheets, tutorials, or advice when servicing a machine. This is the first step toward moving critical industry toward Industry 4.0, and doing it in a safe and secure manner.