How to Scale Smart City Apps with Containerization
Smart cities present interesting problems of scale. The list of applications is practically endless—lighting, emergency services, water treatment, and so on—with each involving thousands of endpoints.
Designing a scalable architecture for these massive systems is a big challenge. Coordinating operations across systems is no small feat, either.
That’s why companies like IoTium are introducing containerized solutions and virtualized networks. These technologies can go a long way toward simplifying the deployment and orchestration of IoT services and applications.
Solving the IoT Deployment Problem
To make IoT applications practical, cities need deployment to be as easy as possible. Ron Victor, founder and CEO of IoTium, says it best: “No one cares about technology. Just connect the machine and make all of this work. I don’t care what you use to do it.”
The same goes for updates. New features and applications must be deployable at the click of a button. “Make sure I don’t have to implement a truck roll every time I want to make a change: That’s the business requirement.”
Security should also be a given. Data must be secured at the source, in transit across multiple networks, and at rest. “Give me assurance I’m 99.999% secure and no one can steal and reroute my data,” says Victor.
Containerization and the Joy of Portability
Recognizing the need for simplicity and security, IoTium made containerization a foundation of its software-defined IoT infrastructure solution. The IoTium solution has three key elements:
- Containerized IoT endpoints
- A network-agnostic transport
- A centralized orchestrator enabling secure zero-touch deployment
Together these elements provide the visibility and control needed for secure IoT deployment, provisioning, and edge analytics at scale (Figure 1).
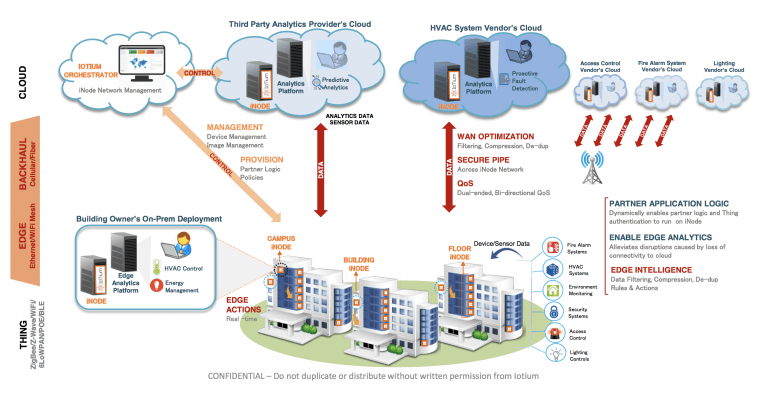
Figure 1. IoTium connects legacy systems at scale. (Source: IoTium)
Containers are a key part of this offering because they provide a known-good environment that ensures applications run as intended. The best-known container technology is the open-source Docker project. Docker is used to automate deployment across different types of hardware—a feat made possible by the abstraction layer that is part of the Docker engine.
Dhawal Tyagi, chief technology officer at IoTium, points out that hardware abstraction has major benefits for cities, which contain many types of legacy infrastructure. “It just makes it a lot easier to coordinate across these systems that may be in your network,” says Tyagi. “You don’t have to worry about small differences between systems.”
In many ways, a container can be compared to a virtual machine. As illustrated in Figure 2, the key difference is that containers share a single OS. As a result, a container can be considerably smaller than a virtual machine.
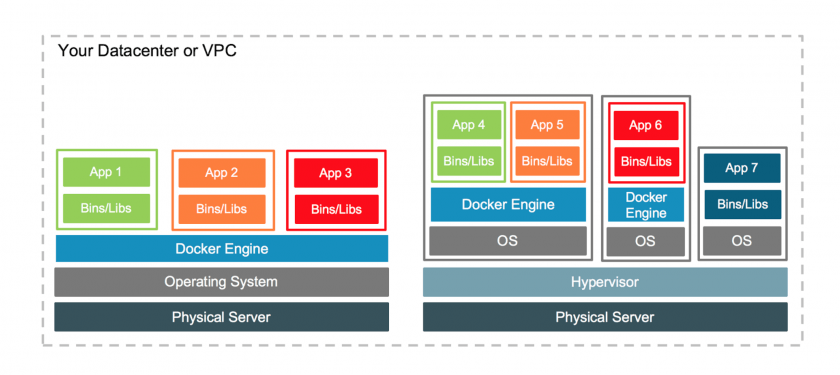
Figure 2. Unlike virtual machines, containers share a single OS. (Source: Docker)
Docker uses the analogy of a house (the virtual machine) and an apartment (the container). Each house has its own infrastructure (plumbing, electricity, heating, security, etc.). In contrast, apartments share infrastructure. Each tenant rents only the resources they need.
This leads to a very different build process. With virtual machines, you start with a full OS, and strip out unwanted components. With containers, it’s the reverse: start with the basics and add only what’s necessary. This helps keep the container light.
Safety Inside the Container
The multi-tenant approach also improves security. Each container can employ custom logic and policies in complete isolation from each other.
IoTium also prioritizes security in its transport layer, which tunnels data from each tenant app directly to a dedicated destination. This way, there is less likelihood of a DDoS attack or rerouting of data. If a data flow is compromised, the hacker won’t be able to affect any other part of the network—even though they may be sharing the same back-end IP data pipe.
“You start with the premise that you will be hacked and then work to minimize the impact of the hack,” says Victor. He explains that this is the reason “we make a change in the networking layer to ensure enhanced security compared to the networking layer that comes standard.”
The transport is designed to seamlessly connect devices, servers, and cloud platforms. To this end, the transport is hardware-, network-, and protocol-agnostic, so it can traverse the various wired and wireless networks within the city.
Orchestrate the Network from A Single Pane
Packaging IoT applications within containers also simplifies orchestration. Because containers virtualize edge devices, users can deploy IoT services and analytics with a single click in the IoTium orchestrator.
The IoTium orchestrator is a centrally managed, single-pane view into the IoT network. The orchestrator is like an app store in that it contains and manages applications and services that can be deployed at will. These include machine learning, encryption, compression, and more.
According to Victor, IoTium’s technology is founded upon a number of core tenets:
- Ensure easy-to-deploy, military-grade security
- Simplify deployment
- Avoid truck rolls and command-line interfaces where a technician needs to be physically present at an asset to acquire data or install updates
- Avoid the need to change IT policy settings or open ports, which can take months for approvals
- Eliminate user names or passwords, a fundamental security weakness
Choosing the Hardware
IoTium’s solution is hardware agnostic and runs on all Intel-based servers and gateways. The minimum requirements for gateways are an Intel® Atom™ processor, 256 Mbytes of RAM, 1 GB of storage, and Ethernet/Wi-Fi/cellular for upstream IP communication.
The gateway forms the main junction at which IoT data is ingested from the various networks and assets. However, IoTium emphasizes scalability of processing and analytics right out to the edge. There, processors such as the Intel® Atom™ processor E3900 series can execute complex analysis and only report back anomalies, to make efficient use of network resources and minimize latency.
As to which hardware vendor to select, IoTium works with Dell, Lanner, Eurotech, and Logic Supply—among others. When choosing a platform, IoTium’s Victor recommends that engineers:
- Account for Internet outages by having enough memory to store a month’s worth of data
- Minimize data flow and WAN costs by running analytics at the edge
- Have enough processing capability at the edge to run encryption, deep packet inspection, and machine learning
- Ensure enough horsepower to last 2 to 5 years of software upgrades
- Ensure hardware root of trust: IoTium can leverage features such as Trusted Platform Module (TPM)
Scaling Smart Cities with Docker
Deploying IoT applications at city scale requires careful planning. To succeed, your design should be easy to deploy, manage, and secure. While there is certainly much room for innovation on all three fronts, working with established technology like Docker—and a purpose-built platform like IoTium’s—is a good place to start.